SLAE64 - 1501
Success in these 7 assignments results in the Pentester Academy's SLAE64 certification.
http://www.securitytube-training.com/online-courses/x8664-assembly-and-shellcoding-on-linux/index.html
Assignment #1: Bind Shell TCP Shellcode
The first assignment is to create a Linux shellcode which:
- binds to a port via TCP
- require a password
- executes a shell on an incoming connection
I started with the TCP Bind shell nasm that I completed while doing the course. This nasm resulted in a binary that was effective and free of null bytes.
I added a read and compare section to this nasm after the 3 dups and before the execve section. It used the read system call and compared the password entered after execution with the one hardcoded into the section ("AAAAAAAA"). If it was the same, then the program continues to the excecve section. If not, then the program exits gracefully.
Here is the read and compare section:
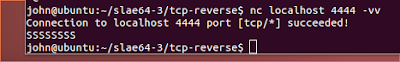
I tested the nasm by compiling, linking, and executing it.
On another terminal I connected to the bind with netcat, then entered the password. This test showed that the nasm was effective.
I confirmed by inspection that the updated nasm was free of null bytes by dumping its obj code.
Then, I extracted the op code using a modified objdump command.
I pasted the op code into the shellcode.c template.
I compiled it using the following gcc command:
$ gcc -fno-stack-protector -z execstack
shellcode.c -o shellcode
I then executed the shellcode binary, connected to the bind, entered the password, and confirmed the shellcode binary got a remote shell by running the linux id command.
It worked. Yay.
I also confirmed that the wrong password caused a graceful exit.
Yay.
Links:









No comments:
Post a Comment