This post is the seventh of 7 exam assignments of the Pentester Academy's x86 Assembly Language and Shellcoding on Linux course. Success in these 7 assignments results in the Pentester Academy's SLAE32 certification.
http://www.securitytube-training.com/online-courses/securitytube-linux-assembly-expert/
SLAE - 901
The files used in this assignment are here:http://www.securitytube-training.com/online-courses/securitytube-linux-assembly-expert/
SLAE - 901
https://github.com/clubjk/SLAE32/tree/master/exam/task7
Assignment 7 Requirements:
- Create a custom crypter like the one shown in the "crypters" video
- Free to use any existing encryption schema
- Can use any programming language
For this assigment I'll use the spritzer encryption algorithm (follow on to AES) to encrypt shellcode as well as decrypt/execute.
I used whitedome's spritzer encryption & decryption/execution script written in C with a modified key.
His script can be found here.
I began by extracting the shellcode from the execve-stack binary.

I copied the shellcode into spritz.c
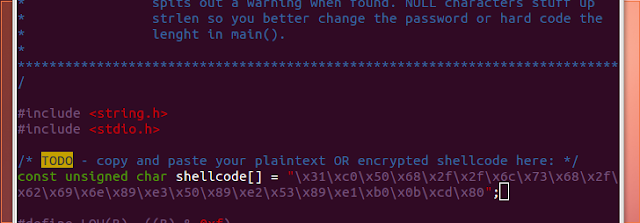
I compiled spritz.c with the following command:
$ gcc -ggdb -fno-stack-protector -z execstack spritz.c -o spritz

Then I executed the script which outputted the encoded shellcode.

I copied the encoded shellcode in spritz.c
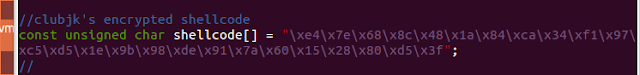
After compiling as I did before, I decoded and executed the shellcode string with the following command:

I used whitedome's spritzer encryption & decryption/execution script written in C with a modified key.
His script can be found here.
I began by extracting the shellcode from the execve-stack binary.

I copied the shellcode into spritz.c

I compiled spritz.c with the following command:
$ gcc -ggdb -fno-stack-protector -z execstack spritz.c -o spritz
Then I executed the script which outputted the encoded shellcode.
I copied the encoded shellcode in spritz.c

After compiling as I did before, I decoded and executed the shellcode string with the following command:
No comments:
Post a Comment